Vivek’s video is here.
This lesson gives you a taste of how broken WEP is. The encryption method sucks.
We’ll break the authentication process, this doesn’t give you access to the network, but it’s the first step. The conclusions will also show that this technique allows you to inject packets of 128 bytes and decrypt the first 128 bytes of any packet. This is all without any brute forcing, the protocol is just broken.
Authentication types
* Open Authentication
* Shared Authentication
* Open Auth:
* no actual authentication, just exchange 2 packets.
* edge cases where it can fail (e.g. MAC filtering)
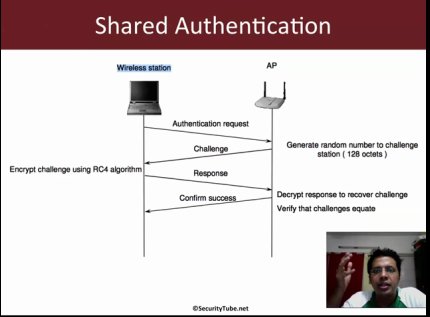
* Shared Authentication
* WEP encryption
* WEP requires 2 things: “IV” (initialisation vector) and “encryption key”
* Uses RC4 encryption algorithm.
* Encrypted stream is XOR’d with cleartext to encrypt.
* Challenge is 128 byte plaintext (random, created by AP)
* Client encrypts it, with random IV.
* Access point checks this against it’s own encryption.
0. Setup an access point and client using WEP encryption, shared authentication.
1. Find the channel of the AP using airodump as before:
airodump-ng mon0 # make a note of the channel and BSSID of the target network
2. Use airodump to capture packets on this channel:
airodump-ng --channel NN mon0 --bssid APBSSID --write demo
3. Connect a client
3.1 Notice that the AUTH column changes and now says “SKA”.
4. Quit airodump. Run wireshark on the capture file:
wireshark demo-01.cap
4.1 Add a filter to show packets to/from our AP and to show auth packets only. You can add auth packets by right clicking and selecting “apply as filter”->”and selected”. You filter should look something like this:
(wlan.addr == APMACADDR) && (wlan.fc.type_subtype == 0x0b)
4.2 You should be able to see 4 packets:
* Check the “Auth SEQ”s you should see packets with SEQ numbers 1,2 and 4 (SEQ3 only shows data).
* SEQ1: The authentication request
* SEQ2: The authentication challenge, containing the challenge text (to be encrypted)
* SEQ3: Encrypted challenge text, with a random IV of the clients choice.
* SEQ4: AP, decrypts the packet. Checks everything is ok and sends success code.
5. Attacker can probe the exchange (like we just did).
5.1 We have the cleartext and the encrypted text.
5.2 Because the encrypted text = cleartext XOR keystream we can extract the keystream easily.
keystream = cleartext XOR encrypted text.
5.3 Uses the IV and the keystream we can authenticate!
5.4 airodump will do it for you. When you made the dump above it should have created a file called demoXXX.xor
5.4.1 It looks like this doesn’t always work, apparently due to broken Access point implementations… (see here)
6. Use aireplay to auth:
aireplay-ng --fakeauth 10 mon0 -e SecurityTube -y demoXXX.xor
6.1 You should see that the authenication is successful.
5. Attacker can probe the exchange (like we just did).
5.1 We have the cleartext and the encrypted text.
5.2 Because the encrypted text = cleartext XOR keystream we can extract the keystream easily.
keystream = cleartext XOR encrypted text.
5.3 Uses the IV and the keystream we can authenticate!
5.4 airodump will do it for you. When you made the dump above it should have created a file called demoXXX.xor
5.4.1 It looks like this doesn’t always work, apparently due to broken Access point implementations…
6. Use aireplay to auth:
aireplay-ng --fakeauth 10 mon0 -e SecurityTube -y demoXXX.xor
6.1 You should see that the authenication is successful.
6.2 Capture the fakeauthentication process with airodump and take a look at it in wireshark.
7. We’ve broken the authenication, so now what?
7.1 We can encrypt small packets and inject them (128bytes)
7.2 IV and keystream can be harvested from packet capture, and we can decrypt first 128 of all packets.
Conclusion: Shared key authentication is broken!